
In response to recent news, we have a few reminders to assist with your remote access preparedness to minimize the disruption to your business.
Make sure your users have access to and are authorized to use the necessary remote access tools, VPN and/or Citrix. If you do not have a remote access account, please request one from your management and they can forward their approval to IT.
If you are working from home and are working with large attachments, they can also be shared using a company approved file sharing system such as Office 365’s OneDrive, Dropbox or Citrix Sharefile. Make sure you are approved to use such service and have the relevant user IDs and passwords. Its best to test them out before you need to use them. Make sure to comply with any security policies in effect for using these services.
Ensure continued access to your 3CX office phone by doing either of these things:
Web meetings or video conferences become critical business tools when working remotely. Make sure you have an account with your company web meeting/video service, with username and password. It is a good idea to test it now to ensure your access is working correctly.
Prepare now and notice the information and supplies you need on a daily basis. Then bring the critical information and supplies home with you in advance so you have them available in the event you need to work remotely. Such items may include:
Company contact information including emergency contact info (including Phone numbers)
Home office supplies such as printer paper, toner and flash drives.
Mailer envelopes large enough to send documents, etc.
Make note of the closest express mailing location near your home and company account information if available
CrossRealms can help set up and manage any or all of the above for you so you can focus on your business and customers.
If you are a current CrossRealms client, please feel free to contact our hotline at 312-278-4445 and choose No.2, or email us at techsupport@newtheme.jlizardo.com
The Business Continuity field is saturated with different solutions, all promising to the do the same thing- keep your business running smoothly and safely post-disaster. But how do you weed through the options to determine which solution is best, and what criteria should you use to do this?
The idea for this blog post came about during a recent visit to a newly acquired client, who was using one of the many solutions for Business Continuity. After asking about the service, our client realized that they had bought it based on affordability, but did not actually analyze the service – and whether it’s good enough for their business. Below, we’ll explore the differences between the above-mentioned solution and Cohesity’s MSP solution (which we currently use at CrossRealms) from technical, process, and financial perspectives. We hope this information can help you think more critically about what’s involved in achieving optimal Business Continuity/Disaster Recovery.
Let’s start with the functional differences between the rival and the Cohesity MSP solution. The following chart breaks it down:

The Cohesity pricing is around $250/TB per month, depending on the size of the backup and requirements, with a one-year minimum commitment. This includes unlimited machine licensing, cloud backup, and SSD local storage for extremely fast recovery. It also includes Tabletop exercises and other business functions necessary for a complete Business Continuity solution.
The rival solution pricing (depending on the reseller) is around $240/TB per month – including the local storage with limited SSD. This also includes unlimited machine licensing and file recovery. It does not include Tabletop exercises, local SSD, or remote connectivity to their data center by the users in case of catastrophic office failure.
Overall, Cohesity outshines competitors with regards to the initial backup/seeding and Test/Dev processes. While it is slightly more expensive, the extra cost is absolutely worth the added benefits.
We hope this post will start a conversation around what should be included or excluded from a Business Continuity plan, and what variables need to be considered when comparing different products. Please comment with any questions or insight – we’d love to hear your thoughts.
Case Study #1: Rural Hospitals and New Technologies: Leading the Way in Business Continuity
The purpose of this series is to shed light onto the evolving nature of Business Continuity, across all industries. If you have an outdated plan, the likelihood of success in a real scenario is most certainly diminished. Many of our clients already have a plan in place, but as we start testing, we have to make changes or redesign the solution altogether. Sometimes the Business Continuity plan is perfect, but does not include changes that were made recently – such as new applications, new business lines/offices, etc.
In each scenario, the customer’s name will not be shared. However, their business and technical challenges as they relate to Business Continuity will be discussed in detail.
Introduction
This case study concerns a rural hospital in the Midwest United States. Rural hospitals face many challenges, mainly in the fact that they serve poorer communities with fewer reimbursements and a lower occupancy rate than their metropolitan competition. Despite this, the hospital was able to surmount these difficulties and achieve an infrastructure that is just as modern and on the leading edge as most major hospital systems.
Background
Our client needed to test their existing Disaster Recovery plan and develop a more comprehensive Business Continuity plan to ensure compliance and seamless healthcare delivery in case of an emergency. This particular client has one main hospital and a network of nine clinics and doctor’s offices.
The primary items of concern were:
After a few days of audit, discussions, and discovery, the following were the results:
Connectivity: The entire hospital and all clinics were on a single Fiber Network which was the only one available in the area. Although there were other providers for Internet access, local fiber was only available from one provider.
Disaster Recovery Site: Their current Business Continuity solution had one of the clinics as a disaster recovery site. This would be disastrous in the event of a fiber network failure, as all locations would go down simultaneously.
Partner Tunnels: Many of their clinical functions required access to their partner networks, which is done through VPN tunnels. This was not provisioned in their current solution.
Medical Services: The primary EMR system was of great concern because their provider would say: “Yes, we are replicating the data and it’s 100% safe, but we cannot test it with you – because, if we do, we have to take the primary system down for a while.” Usually when we hear this, we start thinking “shitshows”. So, we dragged management into it and forced the vendor to run a test. The outcome was a failure. Yes, the data was replicated, and the system could be restored, but it could not be accessed by anyone. The primary reason was the fact that their system replicates and publishes successfully only if the redundant system is on the same network as the primary (an insane – and, sadly – common scenario). A solution to this problem would be to create an “Extended LAN” between the primary site and the backup site.
Telecommunication: The telecommunication system was not a known brand to us, and the manufacturer informed us that the redundancy built into the system only works if both the primary and secondary were connected to the same switch infrastructure.
Solution Proposed
CrossRealms proposed a hot site solution in which three copies of the data and virtual machines will exist: one on their production systems, one on their local network in the form of a Cohesity Virtual Appliance, and one at our Chicago/Vegas Data Centers. This solution allows for instantaneous recovery using the second copy if their local storage or virtual machines are affected. Cohesity’s Virtual Appliance software can publish the environment instantaneously, without having to restore the data to the production system.
The third copy will be used in the case of a major fiber outage or power failure, where their systems will become operational at either of our data centers. The firewall policies and VPN tunnels are preconfigured – including having a read-only copy of their Active Directory environment – which will provide up-to-the-minute replication of their authentication and authorization services.
The following are items still in progress:
Lessons Learned
The following are our most important lessons learned through working with this client:
This past month one of our clients experienced a security compromise with their phone system, where 3 extensions had their credentials swiped. Among the information taken was the remote phone login information, including username, extension and password for their 3CX phone system.
Our first tip off of the attack was the mass amount of international calls being made. We quickly realized that this was not your traditional voicemail attack, or SIP viscous scanner attack because the signature of it was different (more below). To alleviate the situation we immediately changed their login credentials, but to our surprise the attack happened again with the same extensions within minutes of us changing their configuration.
For those of you thinking that the issue can be related to a simple or easy username and password (extension number and a simple 7-digit password), that wouldn’t be the case here. It’s important to note that with 3CX version 15.5 and higher, the login credentials are randomized and do not include the extension id, which makes it a lot harder to guess or brute force attack.
We locked down International dialing while we investigated the issue, and our next target was the server’s operating system. We wasted hours sifting through the logs to see if there were any signs of attack, but absolutely none were present. We next checked the firewall and again saw no signs of attack– so how was this happening? How were they able to figure out the user ID and password so quickly and without triggering the built-in protections that 3CX has, like blacklisting IP addresses and preventing password guessing attempts?
Right back to square one, we needed more information. After contacting different contacts of the client, we found out that the three extensions were present at an International venue, which interestingly enough, was the target of all the International calls!!! Phew, finally a decent clue. Under the assumption of a rogue wireless access point present at the hotel, we asked them to switch to VPN before using their extension, which stopped any new authentication fields from being guessed – – –
While we were able to get our client up and running again, there was something a bit more interesting going on here. The hackers were using a program to establish connections and then use those connections to allow people to dial an International country on the cheap (margins here are extraordinary). That program is using an identifier “user_agent” when establishing a connection to make the calls. If we filter for that, they will have to redo their programming before they can launch the attack again, which proved to be a quick and instantaneous end to this attack irrespective of source– even if they acquire the necessary credentials.
Here’s how I would deal with this next time, in 3CX you can follow the following steps:
Go to
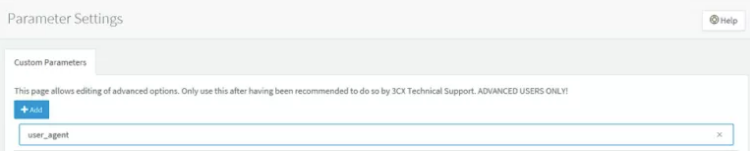
3. Filter for “user_agent”
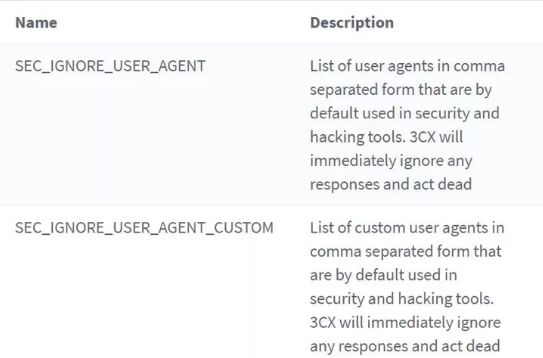
4. Add the user agent used (The Signature) in the attack to either fields and restart services
Eg. The Signature (Ozeki, Gbomba, Mizuphone)

The October Windows Ten Update was released earlier this week, with changes that are sure to suit every user. The update will be available via the Windows website, or will begin to sneak onto Windows users screen as a reminder within the next week.
Kicking off this update are these ten new features:
Fewer Restarts
One of the most grating features of previous updates were sudden restarts. Dona Sakar, a Windows Insider, has noted these disruptions, “We heard you… We trained a predictive model that can accurately predict when the right time to restart the device is.” This means that getting up to get a cup of coffee won’t mean coming back to a computer in reboot mode.
Battery Usage
What’s draining your battery? Task Manager has a new feature that will allow you to view how much battery each app and program is using, best for identifying that excessive power gobbler.
Bluetooth Battery
Love your new wireless headphones? With the new update Windows users will able to see how much battery each of their bluetooth batteries has left.
Text Slider
Among the updates is one that will benefit those who need larger text. Instead of zooming in on a page and distorting the website layout, this text slider will allow the text itself to appear larger.
Snip and Sketch
Bundling multiple applications into one, the “winkey + shift + s” option will allow for a quick screenshot with the possibility of sketching on the saved image. Sharing and printing the saved clipboard image has gotten easier.
Phone Sync
Texting doesn’t have to stop at your phone. Syncing your phone has never gotten easier, the Windows update allows for you phone to link to your computer.The new “Your Phone” feature allows for messages and photos to be linked to your Windows 10 device. This means there is no need to transfer large files via Dropbox or email.
As for compatibility, this works best with Androids and is quickly expanding for better functionality with Apple products.
Dark Mode
Dark Mode has expanded to other Windows 10 applications: File Explorer. This fan-favorite dark screen theme has expanded to your search for files.
Cloud Clipboard
Those that have multiple Windows 10 devices will find this feature of the update most useful. With the Cloud Clipboard feature, you can easily have the same files available across all devices. The transition of moving from a work computer to home computer has been simplified with the new update.
Search Preview
Looking for a file just got easier. With this new search preview feature, a user can search within the start menu and will be able view previews of the files. Allowing for an effortless search.
HDR Support
With the gamer in mind, this Windows 10 update will allow for more contrast and vivid colors than ever. While HDR support has been difficult in the past, this update is looking to fix that.
The new update will also allow for ray-tracing, a Nvidia feature that will allow for better gameplay.
My intention with this blog is to create a conversation about the topic of VDI’s (virtual desktop infrastructure) impact on compliance, whether positive or negative. Therefore, please comment with questions and opinions!
I’ve built and used many VDI environments, but VDI’s impact on compliance didn’t occur to me until recently.
I was hired by a client in the financial sector to identify ways of achieving compliance as it relates to devices at the edge and their cloud presence. My conclusion was that we needed to implement a VDI infrastructure, which would prevent anyone from accessing the cloud tenancies unless they originate from certain IP addresses within the organization. At the same time, we would no longer have to worry about “data at the edge” – i.e. devices and handhelds that can contain compliance data and might be subject to theft or information leak.
As we moved forward with the project, I realized there were other benefits of VDI unaccounted for in the original decision to move to a VDI infrastructure:
In a VDI environment, the different virtual instances can be prevented from exchanging data with one another, which is hard to implement in a physical environment
Users access their VDI environment in the same manner regardless of scenario – normal or disaster recovery; no new accommodations, directives or training for end users must be provided in a business continuity situation
VDI can dynamically allocate resources (RAM, CPU, GPU, etc.) for users with varying workloads, such as in computational modeling
VDI can be designed and deployed based on proven reference architecture, rather than making incremental improvements to existing environments
VDI resolves the issue of preventing USB/External drives from leaking data outside the organization
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Forced reboots no longer affect the end user; patches and updates can run at a very aggressive schedule