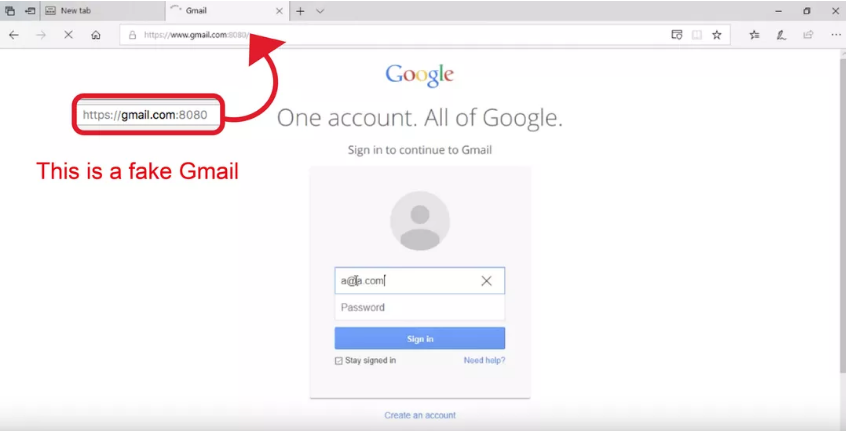
This new phishing attack has gained a level of sophistication that will trick even a trained user. An unpatched URL vulnerability allows a hacker to imitate a website address and then acquire information through a fake login portal.
The URL vulnerability was discovered by Rafay Baloch, a security researcher based in Pakistan. Microsoft Edge by Windows and Apple Safari by iOS are the two major browsers affected. While Microsoft has created a patch for the spoof URLs in the previous month– meaning Google Chrome and Mozilla Fox users are in the clear.
Baloch discovered that this vulnerability (CVE-2018-8383) as a result of a race type condition issue: a web browser will allow JavaScript to change the web address in the URL bar while a page is loading.
Here’s how this phishing attack works: hackers are able to load an authentic webpage, allowing for the proper web address to display in the URL bar, and then quickly swap in a more sinister code. Users are then led to what appears to be a legitimate login screen, where usernames and passwords are then captured. This can easily deceive a vigilant user, as the web address doesn’t appear to change drastically.
Any website can be recreated by a hacker with this URL loophole, including Gmail, Facebook, Twitter, and even a large number of banking websites.
Baloch produced a proof-of-concept (PoC) page where he exposed the URL vulnerability on both Microsoft Edge and Safari. Both web pages granted JavaScript access to change the web address in the URL bar while the page was still loading.
Ultimately, it’s best to double-check web addresses, but to also keep an eye on the latest phishing attacks.
To read more about technical details about the phishing attack, read Baloch’s blog.